Cooliris blows up your Web-surfing experience into a larger-than-life graphical experience. It takes the images it finds on nearly any Web site, expands them to super-extra-large size, and then lets you surf through them in a classy scaling interface that we think we last saw in the Iron Man movie. Or maybe it was The Dark Knight.
Whatever the inspiration, there's no doubt that the cross-platform and cross-browser Cooliris puts the "graphic" back in "graphic user interface". Installing it places a button on the Toolbar. When you're on a Cooliris-enabled Web site, click the Cooliris button to activate the Cooliris interface. Your screen will go black, and all the images on the site will zoom past you as if on a roller-coaster. They stop soon after, and from there you can surf the site using the subtly-placed search bar at the top of your monitor. Click on an image to enlarge it. If it's a still image, it simply enlarges. If it's a video, it enlarges and starts playing.
Currently, the plug-in only supports a handful of the most popular graphics-intensive site, such as Facebook, MySpace, YouTube, Picasa, Flickr, and a few others. A WordPress plug-in allows those who use that blogging system to create Cooliris functionality, and there's a Webmaster's guide on the Cooliris site for users who host their own sites. We also noticed occasional stability problems on Internet Explorer, but they were intermittent at best. Installing the add-on is worth it just for the sweeping, futuristic way that images stream by when you browse, even though there might not be much practical application at this point.
Wednesday, December 31, 2008
Cooliris .... transforming browser into 3D cinema !!!
Saturday, December 27, 2008
Acrobat Replacement ...
This is the cheaper replacement of the famous pdf maker software ... Adobe Acrobat ... its Primo PDF ... but the problem is its just a PDF maker not PDF viewer ... so we can't see PDF files , we can just create it ... to view PDF files then we need some other software ... for example Foxit reader !!! Both apps are free and by combining them two , i have replaced requirement of Adobe Acrobat for my system...
More about Primo ...
PrimoPDF converts just about any file type to a PDF, using the source program the file was created with and its print command. Two new changes make the program easier to use and more useful. The interface redesign is definitely easier to navigate, and users can now choose to email the PDF instantly after its creation.
The conversion process from whatever document is on your screen to PDF is quick and efficient. Other features include a security feature, which allows the user to wrap the PDF in 40-bit or 128-bit encryption, PDF merging, and password protection. The user also can restrict editing of the new PDF, leaving comments and making other changes.
More about Foxit Reader ...
Its Incredibly small , the download size of Foxit Reader is just a fraction of Acrobat Reader 20 M size. Its Breezing-fast, When you run Foxit Reader, it launches instantly without any delay. You are not forced to view an annoying splash window displaying company logo, author names, etc. Good Annotation tool , Foxit Reader allows you to draw graphics, highlight text, type text and make notes on a PDF document and then print out or save the annotated document. Save fillable forms after filling them out so you can continue anytime. Good text converter, You may convert the whole PDF document into a simple text file. High security and privacy: Foxit Reader highly respects the security and privacy of users and will never connect to the Internet without users' permission while other PDF readers often silently connect.
Njoy ...
Tuesday, December 23, 2008
IE 7 Emergency ??
Its been not a new thing that we get time to time updates for various softwares that we use and even for our operating systems from their makes , microsoft or apple for example ... and being good computer user we keep automatic update feature "ON" so our operating system gets updated automatically ... right ?? ...
Well , its about a patch for internet explorer 7 that microsoft released just in an overnight !!! the IE7 vulnerability was such a critical that they had to act fast .. according to microsoft , the systems with OS, XP, Vista , server 2003 , server 2008 were effected.
Once exploited the IE , it downloads trojan that modify files and steals personal informations , it also downloads melicious files that infect user's PC.
So if you still haven't downloaded the patch , then its time ....
Njoy ....
Labels: internet, news, vulnerability, windows
Friday, December 19, 2008
Toad ... for windows !!!
Being the best DBMS software of the world Oracle is the most complex and perhaps the most difficult system to work with ... and i realized that when i took database design course for my fall '08 semester .... Well one of the reasons why i felt Oracle difficult is may be because of lacking so called "computer science" background of mine , ( still i don't know why , i always loved database compared to programming ) ... but when our professor told us that if we do our final project using Oracle as DBMS , we will get extra credit , i jumped in !!! .... before that i had tried SQL Server 2000 , ( and now its 2008 version is already in market ) so i was a bit of lacking knowledge about complexity of Oracle ...
Well one of the reasons why i felt Oracle difficult is may be because of lacking so called "computer science" background of mine , ( still i don't know why , i always loved database compared to programming ) ... but when our professor told us that if we do our final project using Oracle as DBMS , we will get extra credit , i jumped in !!! .... before that i had tried SQL Server 2000 , ( and now its 2008 version is already in market ) so i was a bit of lacking knowledge about complexity of Oracle ...
The main problem i faced with Oracle was , there is no GUI at all !!! ... being windows user that made my life miserable at first because , we just can't move a single step without help of Mr. Mouse !! right ??? and i guess Oracle , doesn't even know what mouse is for !! so it took me a while for getting things done .. another thing that always confused me was after defining tables , how do we know primary key or foreign key of the table ?? , and i still don't know how to do that in Oracle ....
And some day , i came to know this software ... Tool for Application Developer a.k.a TOAD ... actually there are bunch of other software are available just for getting things done with Database development and administration. i found TOAD quite handy tool for my works with Oracle , we can access database directly from TOAD with our Oracle login , and so we can do all the boring command line stuff with fully functional GUI !!! ... it has every thing that we ever need to work with any DBMS , weather its Oracle or SQL server or MYSQL or DB2 or anything ...
Njoy ...
Tuesday, December 9, 2008
MEWU - Scene 8 ... Change your Identity !!!

When we do "experiments" sometimes are need to hide ... or say more softly , change our MAC address. And for this , Ubuntu has very hand tool, called MAC Changer.
But first some words about MAC address... Media Access Control a.k.a. MAC is a unique identifier used to identify network adapters weather it is a Ethernet or WiFi or any Bluetooth , all networking hardware has unique ID , and with who's help those devices --- and so --- "USER" of that device can be identified. This method is used in very basic security schemes that includes mobile networks too !!!
Well, i don't wanna ask why would you ever think to change your MAC address but i know there are always "reasons" to change it for sometime. There are number of ways to change it ,
one method is ...
go to your termainal and write ,
sudo gedit /etc/network/interfaces
it will open interface file of network , it should look like ,
auto eth0
iface eth0 inet dhcp
then simply add a line after these two lines , and it will look like this ,
auto eth0
iface eth0 inet dhcp
hwaddress ether 01:02:03:04:05:06
where 01:02:03:04:05:06 is a FAKE MAC address...
sudo /etc/init.d/networking restart
and you will see your "all new" identity.
Friday, November 21, 2008
WiFi SD !!!
SDs are part of our digital life , we find them in many devices that uses them to store anything ... songs , photos , data for example ... and almost all laptops come with SD card readers which make our life even more easy ( oww.... exclude SONY ... they don't belong here ) ... all we need is to put card in reader and get all the data ...
But how if we can transfer data without even taking out SD card !!! or more briefly ... without even making any physical connection of hardwares !!! well , i guess it will make our life even more easy .. right ??? well there are technologies that can help us for data transformation , for example blue-tooth or Infra RED ... but each has its own limitations , some like .. lower transfer rate or less mobility ... but a yeasterday i found one site ... Eye-Fi ... who claims to sell , SD card equiped with their own WiFi transmission capability !!!! ... now thats something really amazing that we can transfer our data from SD card via WiFi ... according to them , it is secure too because they store all information about on which network the card should transmit on that card it self ... but still i am a little worried about security , i don't want everybody around my house get my girl's pics .. on their network :P ...
also the cost is way too high .... the cheapest one is about $ 80 for 2 Gigs ... compared to about $ 10/15 for same size !!! ... but still if you are tech savvy ... may be you can afford that price ...
Njoy ...
Labels: internet
Tuesday, November 11, 2008
Tune up your Windows ...
Not just another optimizer that we find on internet here and there ... this one is good one ... TuneUp Utilities 2008: The complete Windows optimization package.The Highlights: Boosts system performance by de-fragmenting hard drives; Identifies and deletes non-required files; Deactivates unused Windows functions; Effortlessly solves common computer and display problems; Offers more than 400 options to customize Windows; Analyzes the file system and corrects errors; Performs maintenance functions with a single click.
Temp file management, registry cleaners and start-up program controls are the bread-and-butter of these utilities, and these basics work in TuneUp more quickly and easily than most. However, the app also sports great add-on tools you don't usually see in a utility program. It offers a variety of Internet and program-acceleration tweaks as well as Windows performance enhancers. The crash-preventing MemOptimizer, a file shredder, deleted file recovery, and a respectable uninstall utility round out the suite. You even can automate maintenance tasks with the scheduler or tweak Windows' appearance with the styler tool. The built-in RescueCenter can restore all changes completely or one by one.

Between the guts of steel and the stylish, logically arranged interface, TuneUp Utilities suits all users--from complete beginners who will appreciate the one-click optimization to more daring users who will experiment with all the settings.
Njoy...
Friday, November 7, 2008
Web Browsers .... the new battlefront of hackers !!!
Attacks on operating systems may be decreasing since last year, but attacks on applications, incidents of malware, and unwanted software are rising and account for 90 percent of vulnerabilities, according to the Microsoft Security Intelligence Report, released Saturday. Microsoft said 30 percent of the malware was Trojan-based, and China accounted for 50 percent of browser based attacks, while the U.S. was second at 23 percent.
The amount of malware and unwanted software removed from computers increased 43 percent in the first half of the year, according to the 150-page report, now in its fifth installment. Thirty percent of that malware was Trojan-based, usually in the form of a computer worm or virus disguised as another application that erases data, corrupts files, and reinstalls itself after being disabled. China had the highest percentage of browser-based attacks at 50 percent, with the United States following with 23 percent. China's infection rate of 6.6 percent, a 41 percent increase from the second half of 2007, was a bit lower than industry experts expected.
Microsoft suggests consumers and businesses check for and apply software updates on a continuing basis, enable firewalls, and install antivirus and anti-spyware programs that add another layer of protection.The software giant also suggests that consumers refrain from opening links and attachments in e-mails and instant messages -- even if they are from a trusted source -- without first considering the harm that opening may cause.
njoy ...
Tuesday, November 4, 2008
Javascript - hacker's favorite language !!!
Well , like as usual i came across this article ... and it was good to read it ... so i thought to post it here again ....
The demand that the development of web 2.0 has placed on browsers to become more interactive and act as a portal rather than just a viewing platform is opening up new vulnerabilities to unsuspecting users, Itzik Kotler, team leader of the Security Operation Center at Radware, has warned.
As well as developing new signatures and analytic tools for Radware scanning software, Kotler also works on finding new classes of vulnerabilities before they appear in the wild.
One such security hole is in Javascript, which would allow a hacker to copy any file from a user's PC with little chance of detection – something many have considered to be impossible.
Koter demoed the hack, dubbed Jinx, to vnunet.com at this week's RSA security show in London. He showed how the process was done from within the browser itself, not by altering the browser binary, which can be detected by most anti-virus systems, but rather by adding plain HTML code into just one specific file.
According to Koter, this new class of attack will be attractive to cyber-criminals whose existing techniques are increasingly vulnerable to detection because the approach is cross platform and cross browser, allowing the hackers to access systems previously unavailable to them, such as Linux, Mac and mobile.
The problem stems from the fact that internet browsers have quickly moved from being passive text and picture viewers to essentially an operating system in their own right, through interactive services such as user-generated content, hosted applications, web mail and social networks.
"HTML is now like a batch file for everything," said Koter.
"It's only down to shaping and redirecting it from this intended purpose."
He concluded that, although these types of attack are not yet in the wild, security firms and browser developers need to ensure that the increased demand for a more flexible browser does not open the door to hackers.
Njoy
Thursday, October 30, 2008
Eyecandy cursor for Desktop !!
Sick of looking at that same old cursor? Replace your plain old cursor with animated 3D pointers that look good and can be set to perform tricks, like dotting the screen with color when you click or leaving trails of bubbles in its wake.
CursorFX includes a number of nifty cursor options, and more await in Stardock's online user gallery. We love that your cursor changes over before you even close the program.
You can tweak the custom cursor's look and feel and can easily turn the cursor off if you need a reminder of what you've left behind. CursorFX integrates into the Mouse panel, takes only about 1MB of RAM, and does not slow the cursor's movement. This free application is a must-have for upgrading Vista or XP's look.
Njoy ....
Tuesday, October 28, 2008
Beware of What you Type ???
" Keyboard Sniffing " .... a very new kind of sniffing method which can be used to sniff keys pressed by target user on keyboard !!!
Actually it was just an experiment by swiss students to show a new way of cyber attack ... Doctoral students Martin Vuagnoux and Sylvain Pasini from the Security and Cryptography Laboratory at the Swiss Ecole Polytechnique Federale de Lausanne have revealed that the electromagnetic signals produced by every keystroke can be tracked by hackers.
The students claimed that by analyzing the signals produced by keystrokes, they can reproduce what the target typed. Results led the students to claim that keyboards were not safe to transmit sensitive information.
They tested the technology on 11 keyboard models that were connected either by a USB or a PS/2 socket and every keyboard tested was vulnerable to at least one of the four attacks the researchers used. One attack was shown to work over a distance of 20 meters.
The students used a radio antenna in their research to fully or partially recover keystrokes by spotting the electromagnetic radiation emitted when keys were pressed.
Njoy ...
Labels: internet, news, vulnerability
Monday, October 27, 2008
Some routers are susceptible to SNMP injection !!!
yesterday , i was like always wondering here n there on internet found one article on one of my " source of information " ... that ... not all but some routers from popular vendors are vulnerable to SNMP injection ....
But first , what is SNMP , its Simple Network Management Protocol , which is basically used to monitor network attached devices for conditions that warrant administrative attention. Don't mislead from its name , implementation of this protocol is way too difficult...
Penetration Testing Co. .... ProCheckUp surveyed devices from vendors such as Cisco, Proxim, 3Com and ZyXEL which were all found to be vulnerable.
Identified in ProCheckUp's ‘ZyXEL Gateways Vulnerability Research' paper, it
allows hackers to cause a persistent HTML injection condition on the web management console of several ZyXEL Prestige router models. Provided that an attacker has guessed or cracked the write SNMP community string of a device, they would be able to inject malicious code into the administrative web interface by changing the values of OIDs (SNMP MIB objects) that are printed on HTML pages.
The purpose behind injecting malicious code into the web console via SNMP is to fully compromise the device once the page containing the payload is viewed by the administrator.
The company initially suspected that such an attack was possible on a large number of embedded devices in use in the market, and although the SNMP write community string must be guessed or cracked for this attack to work, some devices come with SNMP read/write access enabled by default using common community strings such as ‘public', ‘private', ‘write' and ‘cable-docsis'.
ProCheckUp also claimed that the use of customised but weak SNMP write community strings, and other weaknesses within the devices SNMP stack implementation should be taken into account when evaluating the feasibility of this attack.
Njoy ....
Labels: internet, vulnerability
Friday, October 24, 2008
Converting Ordinary FlashDrive into Smart Drive !!
Flash Drives / Pen Drives / USB Drives , are quite common in use today for easy transferring data to any place ... they gives us access to out files any time , any where ... right ?? During recent time , some smart guys have designed " Smart Drives " which not only carries data but it also carries bunch of software within that USB drive ... imagine that you are forced to work on some junk computer that even don't have required software for your work , or your favorite browser application or any AV installed !!! or just for sake of security you don't want to use browser of that unknown computer ... in this case these Smart Drives becomes very handy ,right ?? most of them use " U3 technology " .... hell, now a days even smarter drives are in market which uses "biometric ID system" , means you need to scan you finger before you access them !!! ( you can assume that in near future, they are gonna introduce face recognition technology in these drives too !!! )
But still these "smart drivers" are bit costlier then ordinary usb drives ... and perhaps it is the only drawback of them ... now you will ask me , " Why ordinary USB can't be U3 smart drive ? " right ?? ... answer is , U3 smart drives are smart because of embedded hardware chip like of CMOS , which ordinary usb drives doesn't have ...
Well, some good guys ( who believes in free software distribution systems ) developed one software, Portable Apps ,which basically can install applications to even ordinary usb drives and make them works same as smart drive ( ahh , please skip that biomatric part ... ) ... this software comes with plenty of useful stuffs like , open office, firefox , thunder bird, pidgin , an antivirus .... in short all opensource and free applications ( and that makes this application free !! )
Give it a try , i am sure you will not be disappointed ...
Njoy ...
Thursday, October 23, 2008
What's Wrong with Aussie Companies ???
A new survey reveals almost 80% of local companies have experienced data breaches in the past five years, with 40% recording between six and 20 breaches.
The Symantec Australian data loss survey shows 59% of businesses suspect they have been the victim of data breaches, but are unable to identify stolen information.
A whopping 34% of respondents report an average breach cost them $5000, while 14% say breaches cost them between $100,000 and $999,999, and 7% over $1 million.
But the main cause of data breaches, the survey reports, was lost laptops at 45%, while human error accounted for 42% of cases. Malicious attacks were responsible for 28% of breaches, while hacking and malware were responsible for 24%.
njoy ...
Labels: news, security, vulnerability
Friday, October 17, 2008
MEWU - Scene 7 ... IDS for my Network ....
Well , its been an age old question from the days when people started using computers on network ... is my network secure ?? ... ah , i don't think that in this world there is any system that can't be penetrated !! unless there is no way to communicate with system other then mouse and keyboard ,without internet or any network ... hell even without FDD or CDD !!! ... because in many cases when system get jeopardized , by the inside man ( and believe me ,there is no way to protect the system from that mole until information gets stolen ) !!! ... anyways .... as a preventive measure , network admins install grid of network activity sensors , with help of Intrusion Detection System a.k.a. IDS .... basic function of IDS is to detect unauthorized attempt to enter network or other kind of activity that is illegal according to what so ever network policy ... Snort is the most famous personal IDS ,system that is used for network monitoring purpose .... it is also IPS , intrusion prevention system , and it works with other softwares such as BASE, OSSIM to provide visual output with good interface ...
For my trial , i have used SNORT with BASE (for front end )and My-SQL (for storing data in to database for analysis) and APACHE2 server ....
Getting Prepared ......
The first thing I like to do is grab all the dependent packages that I can from Synaptic. From the Desktop go to System > Administration > Synaptic Package Manager. Enter your password and select Search.
Search for the following packages and install them:
* Libpcap0.8-dev
* libmysqlclient15-dev
* mysql-client-5.0
* mysql-server-5.0
* bison
* flex
* apache2
* libapache2-mod-php5
* php5-gd
* php5-mysql
* libphp-adodb
* php-pear
Gain Root Privileges ...
From the Desktop go to Applications > Accessories > Terminal and type:
$ sudo -i
$ Then your password.
We need to get one more package here,
# apt-get install libc6-dev g++ gcc
Gathering Resources ...
We want to create a temp directory to download and untar files. I'm going to use edge's structure here. In the terminal window type the following:
# cd /root
# mkdir snorttmp
# cd /root/snorttmp
Let's get snort. The latest version of snort at the time of writing is 2.8.3.
Open a web browser and navigate to http://www.snort.org/dl; right click on the most recent release and copy link location.
In the terminal type:
# wget http://www.snort.org/dl/current/snort-2.8.3.tar.gz
It's time to untar the Snort package and remove the tar file.
# tar -xzvf /root/snorttmp/snort-2.8.3.tar.gz
# rm /root/snorttmp/snort-2.8.3.tar.gz
Get Snort Rules ...
Change directories into the new snort-2.8.3 folder.
# cd /root/snorttmp/snort-2.8.3
Open a web browser and navigate to http://www.snort.org/pub-bin/downloads.cgi.
Scroll down to the "Sourcefire VRT Certified Rules - The Official Snort Rule set (unregistered user release)" section. Right click on the most recent release and copy link location.
If you are a forum member you can get newer rules which are under the "registered user release".
In the terminal type:
# wget http://www.snort.org/pub-bin/downloads.cgi/Download/vrt_pr/snortrules-pr-2.4.tar.gz
Untar the Snort Rules and remove the tar file.
# tar -xzvf /root/snorttmp/snort-2.8.3/snortrules-pr-2.4.tar.gz
# rm /root/snorttmp/snort-2.8.3/snortrules-pr-2.4.tar.gz
Getting PCRE ... Perl Compatible Regular Epressions ...
Change directory back into the snorttmp folder.
# cd /root/snorttmp
Open a web browser and go to http://www.pcre.org.
Click on the link for the newest release, right click on the newest tar.gz package and select copy link (at the time of writing this is pcre-7.8).
In the terminal type:
# wget ftp://ftp.csx.cam.ac.uk/pub/software/programming/pcre/pcre-7.8.tar.gz
Untar PCRE and remove the tar file.
# tar -xzvf /root/snorttmp/pcre-7.8.tar.gz
# rm /root/snorttmp/pcre-7.8.tar.gz
Getting BASE ... Basic Analysis and Security Engine ...
Change directory back into the snorttmp folder.
# cd /root/snorttmp
Open a web browser and go to http://sourceforge.net/project/showfiles.php?group_id=103348.
Click on download then right click on the newest tar.gz package and select copy link (at the time of writing this is base-1.4.1).
In the terminal type:
# wget http://downloads.sourceforge.net/secureideas/base-1.4.1.tar.gz?modtime=1217804205&big_mirror=0
Untar BASE and remove the tar file.
# tar -xzvf /root/snorttmp/base-1.4.1.tar.gz
# rm /root/snorttmp/base-1.4.1.tar.gz
Getting ADOdb ... a database abstraction library for PHP ...
Change directory back into the snorttmp folder.
# cd /root/snorttmp
Open a web browser and go to http://sourceforge.net/project/showfiles.php?group_id=42718.
Click on the download link for adodb-php5-only then right click on the adodb505.tgz package and select copy link (adodb505 is the most recent package at the time of writing).
In the terminal type:
# wget http://downloads.sourceforge.net/adodb/adodb505.tgz?modtime=1215766049&big_mirror=0
Untar ADOdb and remove the tar file.
# tar -xzvf /root/snorttmp/adodb505.tgz
# rm /root/snorttmp/adodb505.tgz
Do an ls to be sure you have all the packages.
# ls /root/snorttmp
Lets have Some Fun !!
a. PCRE install.
# cd /root/snorttmp/pcre-7.8
Here we will do a make/install
# ./configure
# make
# make install
b. Snort install.
# cd /root/snorttmp/snort-2.8.3
Here we will do a make/install
# ./configure -enable-dynamicplugin --with-mysql
# make
# make install
We need to create some folders in /etc for snort to function correctly and copy some files over to them.
# mkdir /etc/snort /etc/snort/rules /var/log/snort
Let's move some files.
# cd /root/snorttmp/snort-2.8.3/rules
# cp * /etc/snort/rules/
Let's get the /etc snort files also.
# cd /root/snorttmp/snort-2.8.3/etc
# cp * /etc/snort/
One more file.
# cp /usr/local/lib/libpcre.so.0 /usr/lib
Configuring Snort ...
We need to modify the snort.conf file to suite our needs.
Open /etc/snort/snort.conf with your favorite text editor (nano, vi, vim, gedit etc.).
# gedit /etc/snort/snort.conf
Change "var HOME_NET any" to "var HOME_NET 192.168.1.0/24" (your home network may differ from 192.168.1.0)
Change "var EXTERNAL_NET any" to "var EXTERNAL_NET !$HOME_NET" (this is stating everything except HOME_NET is external)
Change "var RULE_PATE ../rules" to "var RULE_PATH /etc/snort/rules"
Scroll down the list to the section with "# output database: log, mysql, user=", remove the "#" from in front of this line.
Leave the "user=root", change the "password=password" to "password=YOUR_PASSWORD", "dbname=snort"
Make note of the username, password, and dbname. You will need this information when we set up the Mysql db.
Save and quit.
Setting UP My-SQL Database ...
Log into the mysql server.
# mysql -u root -p
Sometimes there is no password set so just hit enter.
If you get a failed logon, try the above command again and enter YOUR_PASSWORD.
If there is no password you need to create a password for the root account.
Note: Once you are in mysql the # is now a mysql>
mysql> SET PASSWORD FOR root@localhost=PASSWORD('YOUR_PASSWORD');
Create the snort database.
mysql> create database snort;
mysql> exit
We will use the snort schema for the layout of the database.
# mysql -D snort -u root -p < /root/snorttmp/snort-2.8.3/schemas/create_mysql We need to comment out a few lines in the web rules before we can test snort, I am unsure if this has been fixed in the subscriber version. Open up /etc/snort/rules/web-misc.rules with your favorite text editor. # gedit /etc/snort/rules/web-misc.rules Comment out line's 97, 98, and 452 with a "#" (no quotes).
Testing Snort ...
we need to be sure that our installation works fine ,so we do a test drive of snort ...
In the terminal type:
# snort -c /etc/snort/snort.conf
If everything went well you should see an ascii pig.
To end the test hit ctrl + c.
Setting up BASE and APACHE2 ...
We have already installed both Apache2 and BASE, all we have to do now is move some files and modify a config file.
Create a file called test.php in /var/www/ with your favorite text editor.
# gedit /var/www/test.php
write in it:
Save and close this file
We need to edit /etc/php5/apache2/php.ini file.
# gedit /etc/php5/apache2/php.ini
You need to add the following under "Dynamic Extensions".
extension=mysql.so
extension=gd.so
Restart Apache2.
# /etc/init.d/apache2 restart
Get the ip address of the machine you are working on.
# ifconfig -a
Open a web browser and go to http://YOUR.IP.ADDRESS/test.php.
If everything went well, you will have PHP information displayed. Moving more files...
We need to move ADOdb into the /var/www directory.
# mv /root/snorttmp/adodb505 /var/www/
Let's make a directory in www and move BASE.
# mkdir /var/www/web
# mv /root/snorttmp/base-1.4.1 /var/www/web/
We need to temporarily enable writing to the base-1.4.1 folder for setup.
# chmod 757 /var/www/web/base-1.4.1
We also need to modify a PHP setup file using your favorite text editor.
# vim /var/www/web/base-1.4.1/setup/setup1.php
Find the line that says "base_header" and change it to "header".
Save and exit.
We want the graphs in base to work so we need to install a few pear extensions.
# pear install Image_Color
# pear install Image_Canvas-alpha
# pear install Image_Graph-alpha
BASE Setup via the web....
Open a web browser and navigate to http://YOUR.IP.ADDRESS/web/base-1.4.1/setup.
Click continue on the first page.
Step 1 of 5: Enter the path to ADODB.
This is /var/www/adodb505.
Step 2 of 5:
Database type = MySQL, Database name = snort, Database Host = localhost, Database username = root, Database Password = YOUR_PASSWORD
Step 3 of 5: If you want to use authentication enter a username and password here.
Step 4 of 5: Click on Create BASE AG.
Step 5 of 5: one step 4 is done at the bottom click on Now continue to step 5.
Bookmark this page.
Change the permissions back on the /var/www/web/base-1.4.1 folder.
# chmod 775 /var/www/web/base-1.4.1
We are DONE !!!
To start Snort in the terminal type:
# snort -c /etc/snort/snort.conf -i eth0 -D
This starts snort using eth0 interface in a daemon mode.
To make sure it is running you can check with the following command:
# ps aux | grep snort
If it's running you will see an entry similar to snort -c /etc/snort/snort.conf -i eth0 -D.
Finally , to see the snort in action , we can run BASE engine , by going that page we are using to run via apache server ...
phewww ... after following brain twisting procedures i was finally able to setup my personal IDS using SNORT ,which took me almost more then one and half hour ... i hope this walkthrough will work for you guys too ...
njoy ....
Thursday, October 16, 2008
Cloud Computing ..... future of Computing !!!
The Cloud ... refers to Internet itself ... and so Cloud Computing means , computing with help of internet itself ... The roots of cloud computing is lying near early 90s ... where they first ever thought that internet can be used to provide various services !!! ( at that time it was used to run ATMs ) ...
But people dared to go beyond it and tried to visualize the world where all the applications run via internet .. even operating system's basic functions too !! , just Imagine you are playing free cell on internet !!! well .. its quite possible ... at present the Cloud computing offers various services like .. Web 2.0 applications ... software as a service ... tried google apps ??? ... no application installed on system ... all software and data are stored on server !!!
It has been said that Microsoft and some other companies are working to develop very first OS that is based on Cloud Computing ... who know ... may be after a year or a two .. we might be using it !!!
Cloud computing is getting fame at present time ... because of couple of unbeatable features that no one else can offer .... features like ... its very cheap to use ... device and location independence ... scalability ... but still there are some features that need to gain confidence of users like ... less security ... how can you feel secure about your data stored online rather then on your hard driver ?? ... and unreliability ... what if the application server goes down ?? or if you have insufficient bandwidth ?? ...
But the basic and main requirement of cloud computing is ... guess what ??? ..... ya .. its High speed internet ... right ?? and bad news is the total percentage of internet uses are about nealy 21% ... and even worse is , all these 21% aren't using high speed internet like DSL or Cable ... high number of people are still using DialUp .. i guess its pretty slow for cloud computing ... and i think it is the only reason whey cloud computing is not much popular ....
Labels: cloud computing, internet
Wednesday, October 15, 2008
Subsubstitute of MS Office !!!
If you are not knowing Microsoft's super famous product MS Office ... then i think you are from the planets of Wookiees ... ( hell , even they must be knowing it !!! ) ...
Actually , its about one the rival application that has got a bit of fame from its first release , its Open Office from Sun !!! ... like we know , its an open source project started by Sun microsystems ... which was originally known as Star Office , a product from German company brought by Sun during end of millennium ...
Open Office , supports all file formats created by MS Office , like .doc , .xls , .ppt etc ... which we use most of the time ... and moreover its all Freeeeee !! , thats the key point to its success , because everybody likes free ... right ??
Recently they have release Open Office 3 ... the latest beta of OO, and like expected from sun .... it supports all extensions created by MS Office 2008 , like .docx and .xlsx .... as it was major hit , the office download site got crashed right on the first day of beta release !!! ... and still its down ( ahh ... but still you can download it ) ...
If you are into search of Open Source software or something that is simply free and yet as powerful as MS Office .. then this is worth trying....
njoy ....
Thursday, October 9, 2008
List the Folders ...
Sometimes , when i have lots of files under one folder and i want to just get the name of all files ... Or in another case , i have an external HDD of massive 750Gigs ... and i simply want to list all the folders and subfolders and files in it ... just imagine you are big fan of RnB and have big collection and you want to make cataloge of it ??? .... then it is really pain in a$$ to first read name and then type in text editor ... and it takes hell lot time too .. right ??
Well , for me , it was just a few mouse clicks ... with help of this junk ... Print Folders .... it simply prints all files / folders / sub folders ( or any of them ) to simple text file .. or a html file ... so we can save it too and read / review it later !!! ...
This tool is pretty handy when you have massive number of files !!!
Njoy ....
Wednesday, October 8, 2008
Surf Anonymously !!!
In present time , its really easy for anyone to get someone else' identity on internet , even you IP can reveal you geographical location or worse , your identity !!! Like , we know , any computer on internet is identified by its IP address , and hence all websites use this numbers to identify users ... But with just that information of IP number , wrong guys can make your life hell !!!
Or consider another scenario ... suppose some sites like facebook or myspace are restricted to access from your place !!! .. ( its very common .. right ?? ) ... in that case what you can do ??
For this , we can use PROXY sites .... from webster's dictionary .... Proxy means ...
the agency, function, or office of a deputy who acts as a substitute for another.
authority, power to act for another
a person authorized to work for another
anyways ... in general ... proxies can be used to just surf anonymously or to bypass internet restrictions ....
Njoy ...
Labels: internet, software, technology
Monday, October 6, 2008
The DarkSide of LinuX !!!!
BT3 comes as a Live CD , bt they have USB version too !!! BT3 is having all famous tools that are used to test system defence like , kismet , ASS or any you name it and they have it here ... But like they say , they are not professional guys so don't expect any professional help from 'em , but their forum is really great help ...
Sure its worth of try if you want to "test" .... Yours n/w or ... " other's " n/w ..... geeee ... its not wrong to test other's too ... right ?? ... well , its another point of dicussion .... if you want to try BT3 , here is the link to download it ...
Njoy ...
Thursday, October 2, 2008
What is "ClickJacking" ??
"Click Jacking" ..... well , it means almost same to the word it resembles .... Hijacking ...
It is couple of the flaws discovered by researchers , would enable an attacker to make a user click on a virtually invisible, or only briefly visible, link instead of a legitimate one. This kind of weakness would be a goldmine for phishers and could provide a springboard for a host of other attacks. And for this each site needed to be updated but its almost impossible, to guys who have found it contacted vendors of browsers to fix it up ... people says , its been age old vulnerability of browsers but just under-appreciated and now came up with more serious problems ...
But , the details of this vulnerability hasn't been disclosed publicly just to give time to companies to fix this problem and not to give spammers and hackers an open ground ...
njoy ....
Sunday, September 28, 2008
Lyrics with Song ...
Sometimes i just wanted to do karaoke .. ( err , only when i am alone !!! ) ... i always need to search lyrics for songs on internet and then match it track by track to that song ... but its real pain in a$$ ... yesterday , when i was browsing internet , i found one junk software , called ... "mini Lyrics" ...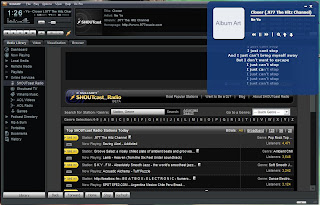
When i did test drive with my winamp's shoutcast radio .... i was just amazed !!! , this software is awesome ... even with internet radio , it works superfine , and as they change track , this junk gets new song's lyrics automatically almost in no time !!! , and yet its very resource low application that is the plus point .... it supports lots of other popular players , like , winamp , jetaudio , foobar , windows media player , real player and many more .... also , its skinable , so you have have feel and look of your choise ...
better try your self ...
Njoy ...
Friday, September 26, 2008
Beware of PDFs ???
The Portable Document Format ... PDF .... perhaps the most used way to share or distribute documents on internet ... its because it provides , portability , security and authoritativeness for documents , right ?? You might be surprised to read that , Acrobat Reader is perhaps the most downloaded and uses application among internet users ... reason ?? , because , its free , popular and ultra light .. ( err not by "weight" , by performance and resource consumption ) ...
Secure Computing’s Anti-Malware Research Labs spotted a new and yet unknown exploit toolkit which exclusively targets Adobe’s PDF format !!! This new toolkit targets only PDFs, no other exploits are used to leverage vulnerabilities. Typical functions like caching the already infected users are deployed by this toolkit on the sever-side. Whenever a malicious PDF exploit is successfully delivered, the victim’s IP address is remembered for a certain period of time. During this “ban time” the exploit is not delivered to that IP again, which is another burden for incident handling. Malware spreaders have put this kind of exploits to their arsenal of malicious weapons for a longer time already. The “Tibs” group of malware, for example, is known for planting malicious IFRAMEs onto infected legitimate web sites and having them refer back to their exploit servers. Dissecting the shellcode shows that the payload of the exploits tries to load more malware and the different number per exploit appears to be a kind of affilation ID to keep some statistics and track their different malware campaigns.
But , Secure Anti-Malware customers are protected since such PDF exploits are blocked proactively as “Script.Shellcode.Gen”!!! And don’t forget to not only patch the latested operating system and browser vulnerabilities, but also keep an eye on third-party browser plugins like Adobe Reader, Flash Player and QuickTime.
Better be carefull out there ....
Njoy ...
Labels: internet, vulnerability
Thursday, September 25, 2008
Make the way for P4P .......
Peer to Peer a.k.a. P2P technology is on main stream now a days .... but like all of us know, it has recently raised questions about network neutrality 'coz of ISPs like Comcast which tried to throttle p2p activities of users .... its not case of only one ISP , in USA all major ISPs are worried for their large bandwidth consumption and congested networks because of P2P usages ...
So some smartass guys of "Verizon" have formed a group to develope a new kind of protocol for this kind of file sharing ... they call it P4P ... "Proactive network Provider Participation for P2P" ... that ultimately aims to de crease backbone traffic and bring down network operation costs by enabling service providers to communicate information about network conditions to client applications for the purpose of facilitating improved P2P file transfer performance. Instead of selecting peers at random, the P4P protocol leverages network topology data so that peers can be selected in a manner that increases routing efficiency. Verizon believes that P2P technology is moving into the mainstream and is being legitimized for large-scale commercial content delivery. The company sees P4P as a way to enable broader commercial adoption of P2P tech while unclogging the tubes and relieving network congestion.
crease backbone traffic and bring down network operation costs by enabling service providers to communicate information about network conditions to client applications for the purpose of facilitating improved P2P file transfer performance. Instead of selecting peers at random, the P4P protocol leverages network topology data so that peers can be selected in a manner that increases routing efficiency. Verizon believes that P2P technology is moving into the mainstream and is being legitimized for large-scale commercial content delivery. The company sees P4P as a way to enable broader commercial adoption of P2P tech while unclogging the tubes and relieving network congestion.
In a paper published by the P4P group, "P4P: Explicit Communications for Cooperative Control Between P2P and Network Providers," researchers look at some of the unique advantages of P4P compared to other solutions. The report notes that traffic-shaping technologies that rely on deep packet inspection to throttle P2P are easily thwarted by client applications that encrypt traffic and use dynamic ports to evade identification. Without the cooperation of the actual P2P services, the report says, no solution will succeed. "It remains unclear whether in the long run traffic shaping can effectively control the bandwidth consumption of P2P applications and reduce provider's operational costs," the paper's authors note. "By enabling explicit communication between P2P and the network, P4P can enable applications to use network status information to reduce backbone traffic and lower operation costs."
I think its better option chosen by Verizon , then its competitor AT&T ... who want to spy on their own network users for use of this kind of file sharing which violates copyright infringment !!! ... ( damn .... what the hack ??? ... sounds like a private police ... right ??) ... well its another issue ... we'll talk about it someother day ....
njoy ....
Labels: internet, news, technology
Wednesday, September 24, 2008
MEWU - Scene 6 ... Want to replace FireFox ??
Well , like you all know , FF is default browser in Ubuntu ... No doubt FF is da best in performance then any other browsers .... ( mostly !!! ) ... But still , its not "catchy" !!! .... yup , its very true ... There are many many other substitutes available for Ubuntu and linux itself .... but all are same dull like FF ... But there is one eye candy browser exists for linux which makes me think twice ... its one and only ... FLOCK ... the social browser !!!
I think , people who are using internet , might be knowing already about this browser , actually its lot more then simple browser , just imagine netscape nevigator with look of chrome !!! .. ( err , i think netscape nevigator is almost obsolate now , but i still remember using that all in one browser which had ability to play a role of web browser to mail manager !!! .. it was late years of millenium , ahh beautiful old days ) ... gasp ... anyways , here we are talking about this new shiney browser ... with its help you can also do things like writing blogs offline and then upload em on supported services of flock ... i mean , all web 2.0 stuffs !!!
Unfortunately they haven't got any .DEB package for flock yet ... so there is not direct way to install it in Debian Systems like Ubuntu ... but there are "ways" for getting things done !!!
- Download Flock 2 and select “Save File” to store it on your Desktop.
- Open a terminal and run:
sudo tar -C /opt -xzvf Desktop/flock-*.tar.gz - Create a link to the new browser within your PATH:
sudo ln -s /opt/flock/flock /usr/bin/flock-browser - copy the following into a new file by command ,
sudo gedit /usr/share/applications/flock.desktop
[Desktop Entry]
Encoding=UTF-8
Name=Flock
Comment=Flock Web Browser
Exec=flock-browser
Icon=/opt/flock/icons/mozicon128.png
StartupNotify=true
Terminal=false
Type=Application
Categories=Applications;Network
You should now have a new entry in your Applications menu called “Flock Web Browser” (your menu may need to refresh first). You can also launch the browser from the terminal using the command:
flock-browser
If Anytime there is a Flock Browser update you should be able to safely repeat steps 1 and 2 and you’re set.
Njoy ....
Sunday, September 21, 2008
(Un)Official Chrome for Linux !!!


Find the Bots in your computer !!!
Well ... they are not acutally made of machines like we saw in terminator ( ... btw .. T2 was one of mine fav movie .. ) , its technically some kind of program or software application that are designed to do some specific works when computer gets connected to internet ... in "common man's " ... ( .. it includes women too !! ) ... a SPYWARE ...
Anyways .... i have been knowing this junk from the time i know how to use internet explorer , and its very reliable .. they call its .. Spybot Search & Destroy ... It can detect and remove a multitude of adware files and modules from your computer. Spybot also can clean program and Web-usage tracks from your system, which is especially useful if you share your computer. Modules chosen for removal can be sent directly to the included file shredder, ensuring complete elimination from your system. For advanced users, it allows you to fix Registry inconsistencies related to adware and to malicious program installations. The handy online-update feature ensures that Spybot always has the most current and complete listings of adware, dialers, and other uninvited system residents.
It has saved my #$* number of times ... so i trust this junk ... but like some have said ... " if you want to do something then do it your self " ... so better try yourself and judge it ..
njoy ....
Sunday, September 14, 2008
MD5 ..... cross check the integrity ...
trust but verify ...
~ronald reagan
When ever we download any file ( setup file for an example ) , we never be sure that its the "original" file from original author . And hence it can be some malicious thing too !!! so guys of internet had been using an integrity checker that is Message Digest Algorithm 5 .. a.k.a. MD5 ... As an Internet standard RFC 1321, MD5 has been employed in a wide variety of security applications, and is also commonly used to check the integrity of files. An MD5 hash is typically expressed as a 32 digit hexadecimal number.
MD5 is basically cryptographic hash function with 128 bit hash value... MD5 digests have been widely used in the software world to provide some assurance that a transferred file has arrived intact. For example, file servers often provide a pre-computed MD5 checksum for the files, so that a user can compare the checksum of the downloaded file to it. Unix-based operating systems include MD5 sum utilities in their distribution packages, whereas Windows users use third-party applications.
However, now that it is easy to generate MD5 collisions, it is possible for the person who created the file to create a second file with the same checksum, so this technique cannot protect against some forms of malicious tampering. Also, in some cases the checksum cannot be trusted (for example, if it was obtained over the same channel as the downloaded file), in which case MD5 can only provide error-checking functionality: it will recognize a corrupt or incomplete download, which becomes more likely when downloading larger files.
To check integrity of downloaded file in Unix/Linux based OS, simply type
md5sum file.name
it will return with some hash values which is then needed to be compared with values provided on site of that software ... but remember that this command has to be run in the folder where that file has been downloaded , no where else ...
for windows .. its a little easy , here hash values are compared with help of a software ... its winMD5sum , an open source and free software .... to check integrity ...
simply right click on the downloaded file and go to "send to" , in it winMD5Sum , it will calculate hash values automatically , now enter values provided by site and click on compare ... if values matches then it will say .. checksum are same ...

so from next time when you download something , better try to be sure that you have not downloaded rouge ...... best luck ...
njoy ....
Free AntiVirus for One Year !!!
There is one company called CA , ( ahh , its the same company makes ERWin , a very popular database modeling software ) is offering one year free subscription to their Antivirus product .. "CA Antivirus 2008" ... its pretty good antivirus with a very good price --- "free" ...
If you're unprotected, viruses can invade through email, downloads, instant messages, and even Web pages. From there, they can erase your files, damage your hard drive, and destroy the information you value most: photos, music, documents, and more. CA Anti-Virus provides comprehensive protection against viruses, worms and Trojan horse programs ....
All you need is to go to their registration page and get registered to get your Serial Key ....
njoy ... and have a safe system ..
Thursday, September 11, 2008
Top 10 Linux Distros !!!
Well , this is for people like me who want to try some new OSes ... just a comparison of popularity of currently available linux distros .... its from very famous sites which is dedicated only to keep track of all available and working linux distros .. distrowatch
1 .... The number one is undoubtedly ... UBUNTU ....
- Pros: Fixed release cycle and support period; novice-friendly; wealth of documentation, both official and user-contributed
- Cons: Some of Ubuntu's own software (e.g. Launchpad, Rosetta) are proprietary; lacks compatibility with Debian
- Software package management: Advanced Package Tool (APT) using DEB packages
- Available editions: Ubuntu,Kubuntu,Edubuntu & Xubuntu for 32-bit (i386) and 64-bit (x86_64) processors; Ubuntu Server edition also for SPARC processors
- Suggested Ubuntu-based alternatives: Linux Mint(desktop), Freespire (desktop), gNewSense (free software)
2 ... the 2nd is OpenSuSE ... from novell
- Pros: Comprehensive and intuitive configuration tool; large repository of software packages, excellent web site infrastructure and printed documentation
- Cons: Novell's patent deal with Microsoft in November 2006 seemingly legitimised Microsoft's intellectual property claims over Linux; its resource-heavy desktop setup and graphical utilities are sometimes seen as "bloated and slow"
- Software package management: YaST graphical and command line utility using RPM packages
- Available editions: openSuSE for 32-bit (i386), 64-bit (x86_64) and PowerPC (ppc) processors (also a non-installable live DVD edition); suse linux enterprise Desktop/Server for i586, IA64, PowerPC, s390, s390x and x86_64 architectures
3 ... another famous distro is ... fedora
- Pros: Highly innovative; outstanding security features; large number of supported packages; strict adherence to the Free Software philosophy
- Cons: Fedora's priorities tend to lean towards enterprise features, rather than desktop usability
- Software package management: YUM graphical and command line utility using RPM packages
- Available editions: Fedora for 32-bit (i386), 64-bit (x86_64) and PowerPC (ppc) processors; RedHat Enterprise Linux for i386, IA64, PowerPC, s390x and x86_64 architectures; also live CD and live DVD editions
- Suggested Fedora-based alternatives: Blag Linux and GNU(desktop, free software),Berry Linux (live CD),Yellow Dog Linux (Apple's PowerPC-based systems)
- Suggested Red Hat-based alternatives: CentOS, Scientific Linux, StartCom Enterprise Linux, Lineox
- Pros: Very stable; remarkable quality control; includes over 20,000 software packages; supports more processor architectures than any other Linux distribution
- Cons: Conservative - due to its support for many processor architectures, newest technologies are not always included; slow release cycle (one stable release every 1 - 3 years); discussions on developer mailing lists and blogs can be uncultured at times
- Software package management: Advanced Package Tool (APT) using DEB packages
- Available editions: Installation CD/DVD and live CD images for 11 processor architectures, including all 32-bit and 64-bit processors from Intel, AMD, Power and others
- Suggested Debian-based alternatives: MEPIS Linux, Ubuntu, Damn Small Linux, Knoppix , Sidux, Dreamlinux, Elive,Xandros,64 Studio
5 ... Mandriva ... huh ?? , never heard before ... but they says its famous !! ..
- Pros: Beginner-friendly, especially the commercial editions; excellent central configuration utility; very good out-of-the-box support for dozens of languages; installable live CD
- Cons: The company's customer service has developed bad reputation over the years; complex, confusing web site infrastructure; dropping popularity due to its commercial nature and unpopular corporate decisions in the past
- Software package management: URPMI with Rpmdrake (a graphical front-end for URPMI) using RPM packages; "SMART" available as an alternative method
- Available editions: Freely downloadable Mandriva Free and One editions for 32-bit (i386) and 64-bit (x86_64) processors; commercial Mandriva Discovery, PowerPack and PowerPack Plus editions for 32-bit (i386) and 64-bit (x86_64); also high-end "Corporate" solutions for desktops, servers and firewalls, all with long-term support options
- Suggested Mandriva-based alternatives: PCLinuxOS(desktop), MCNLive(live CD)
- Pros: Out-of-the-box support for graphics drivers, browser plugins and media codecs; fast boot times; up-to-date software
- Cons: No 64-bit edition offered; no out-of-the-box support for non-English languages; lacks release planning
- Software package management: Advanced Package Tool (APT) using RPM packages
- Available editions: MiniMe, Junior and BigDaddy editions for 32-bit (i586) processor architectures
- Suggested PCLinuxOS-based alternative: SAM Linux Desktop
7 ... MEPIS ... ah , why its on 7 , it should be on 5 ..
- Pros: Beginner-friendly; excellent hardware auto-detection and support; intuitive, installable live CD
- Cons: Software in its repositories not always up-to-date, lacks development roadmap
- Software package management: Advanced Package Tool (APT) using DEB packages
- Available editions: Simply MEPIS for 32-bit (i386) and 64-bit (x86_64) processors
8 ... Knoppix .... this one is nice ...
- Pros: Unparalleled hardware auto-detection and auto-configuration; portable operating system that can be used for rescue, demonstration and testing tasks; provides a hard-disk installation script
- Cons: Recent releases somewhat buggy; lack of polish and unification of menus across the different desktop environments; slow when run from DVD
- Software package management: Advanced Package Tool (APT) using DEB packages
- Available editions: Live CD and Live DVD editions for 32-bit (i386) processors
- Suggested Debian/KNOPPIX-based alternatives: Damn Small Linux, sidux,Xandros Desktop, Elive, Dreamlinux, Parsix GNU/Linux, grml
9 ... Slack ware .... it is the most oldest surving linux from year of '92 !! it should be on top , but i think its not as much popular as others ....
- Pros: Highly stable, clean and bug-free, strong adherence to UNIX principles
- Cons: Limited number of officially supported applications; conservative in terms of base package selection; complex upgrade procedure; no official 64-bit edition
- Software package management: "pkgtools" using TGZ (TAR.GZ) packages
- Available editions: Installation CDs and DVD for 32-bit (i486) processors
- Suggested Slackware-based alternatives: Zenawalk Linux (desktop), Vector Linux(desktop), SLAX(live CD),Slamd64 Linux(64-bit),Bluewhite64 Linux (64-bit),Wolvix (desktop, live CD),GoblinX (desktop, live CD)
- Other distributions with similar philosophies: Arch Linux ,Frugalware Linux, KateOS
10 ... Gentoo ....
- Pros: Excellent software management infrastructure, unparalleled customisation and tweaking options, superb online documentation
- Cons: Occasional instability and risk of breakdown, the project suffers from lack of directions and frequent infighting between its developers
- Software package management: "Portage" using source (SRC) packages
- Available editions: Minimal installation CD and live CD (with GNOME) for Alpha, AMD64, HPPA, IA64, MIPS, PPC, SPARC and x86 processors; also "stages" for manual installation from command line
- Suggested Gentoo-based alternatives: Sabayon Linux(desktop, live CD/DVD), VLOS(desktop), Ututo(desktop, free software only)
- Other source-based distributions: Lunar Linux,Source Mage GNU/Linux, Sorcerer ,Linux from Scratch
- Pros: Fast and stable; availability of over 15,000 software applications (or "ports") for installation; very good documentation
- Cons: Tends to lag behind Linux in terms of support for exotic hardware, limited availability of commercial applications; lacks graphical configuration tools
- Software package management: A complete command-line package management infrastructure using either binary packages or source-based "ports" (TBZ)
- Available editions: Installation CDs for Alpha, AMD64, i386, IA64, PC98 and SPARC64 processors
- Suggested FreeBSD-based alternatives: PC-BSD (desktop), DesktopBSD (desktop), FreeSBIE(live CD)
- Other BSD alternatives: OpenBSD,NetBSD, DragonFly BSD
that is it ....
njoy reading ... and don't forget to try atleast one of above distros ...
Labels: linux
Useful Add-Ons for FireFox ...
Here is the list of couple of very useful AddOns for FireFox ..
AdBlock Plus
a filter subscription when Adblock Plus starts up the first time, then even this simple task will usually be unnecessary: the filter subscription will block most advertisements fully automatically
 Colors every tab in a different color and makes them easy to distinguish while beautifying the overall appearance of the interface. An essential...
Colors every tab in a different color and makes them easy to distinguish while beautifying the overall appearance of the interface. An essential...
Flash Block
This plunging blocks any flash contains on web page. which is quite useful if you want to save bandwidth.
Tab mix plus
you can have as many tabs as you like. It includes such features as duplicating tabs, controlling tab focus, tab clicking options, undo closed tabs and windows, plus much more. It also includes a full-featured session manager with crash recovery that can save and restore combinations of opened tabs and windows.
McAfee SiteAdvisor for Firefox 26.5
SiteAdvisor helps protect you from all kinds of Web-based security threats including spyware, adware, spam, viruses, browser-based attacks, phishing, online fraud and identity theft.
Download StatusbarWeb developments :
FireBug
======
allows you to debug the scripts. useful if you are doing web development. ( where you don't want to invest in heavy duty, high cost tools)
View source
========
better then conventional source code viewer. this shows coloured
Internet Security :
Local Link
=======
this blocks any script execution from webpage. like scripts which can execute lunches something. you can block/give permission by using local link ( which is a strong consequence of Internet explorer ).
njoy ....
Tuesday, September 9, 2008
MEWU - Scene 5 ... Playing With Shark !?!?
Owww, its not that always hungry long saw toothed terrifying wild creature from that movie JAWS .... its just a network analysis tool, Wire Shark , but its just same powerful as jaws of shark !!!... it is widely used to understand how internet itself that is , hidden behind web browsers and messengers and lots of other web based applications ... it shows us the way how protocols are stacked up or what protcol messages are interexchanged between client and server , when we do any kind of network transactions ...
Wireshark has a rich feature set which includes the following:
- Deep Inspection of hundered of protocols, with more being added all the time
- Live capture and offline analysis
- Standard three-pane packet browser
- Multi-platform: Runs on Windows, Linux, OS X, Solaris, FreeBSD, NetBSD, and many others
- Captured network data can be browsed via a GUI, or via the TTY-mode TShark utility
- The most powerful display filters in the industry
- Rich VoIP analysis
- Read/write many different capture file formats: tcpdump (libpcap), Catapult DCT2000, Cisco Secure IDS iplog, Microsoft Network Monitor, Network General Sniffer® (compressed and uncompressed), Sniffer® Pro, and NetXray®, Network Instruments Observer, Novell LANalyzer, RADCOM WAN/LAN Analyzer, Shomiti/Finisar Surveyor, Tektronix K12xx, Visual Networks Visual UpTime, WildPackets EtherPeek/TokenPeek/AiroPeek, and many others
- Capture files compressed with gzip can be decompressed on the fly
- Live data can be read from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others (depending on your platfrom)
- Decryption support for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
- Coloring rules can be applied to the packet list for quick, intuitive analysis
- Output can be exported to XML, PostScript®, CSV, or plain text

To , install it in Ubuntu , search synaptic manager for "wireshark" , and select to install it ...
Or, type ,
sudp apt-get install wireshark
it will work fine too ... but to run wireshark you must be needed to have administrator privillages .. because without administrator privillage you will not be able to get any interface to capture packets .... so , to run it , you have to type at terminal ...
sudo wireshark
and it will work just fine ....
that is it , have a good play with shark ...
njoy ...
Sunday, September 7, 2008
MEWU - Scene 4 ... GUI Firewall ..
Hmm, like all you know , Linux is comparatively safer then other dumb OSes ... ( do i need to name 'em ?? ) ... so linux is not required to have an AV products ... also , It has built-in Firewall , which is Ip-Tables ...which are basically rules written manually !!! , but its little difficult for "common guy" like me to write syntexes and codes .. ah it just makes me nervous ... so i prefer more GUI ... well you can say its "side-effect" on me due to overdoze of "window" medicine !! ... so this front-end software is very handy for me ... they call it .."fire starter" ... sort of ..
Well, Firestarter is basically just a front end ... it still uses Ip-tables as back end .. means , since Ip-tables are little geeky to use, Firestarter makes life eazy by providing Graphical interface of Ip-tables !!!
we can install in via , synaptic manger ... just search for "firestarter" and you get it !!!
or in terminal type ..
sudo apt-get install firestarter
it will work fine too ... at first time you will be needed to provide the name of interface for which you want this firewall to work ... i use wifi mainly so i had chosen, ATH0 ( i think, ath0 is for atheros cards only !!! ) ... and you are all set ... but again , this GUI doesn't load on startups ... ( don't mix gui with original firewalls ... because the Ip-tables itself gets loaded once n/w gets established but in deamon/background ) , so to start firestarter at startup you can do any way you like , but the way i preferred is through , system -> preferances -> sessions , in startups , ADD , choose name and description as you like , and for command , write ,
gksudo firestarter
so , next time when you will boot , it will ask for password when it will be loaded i think its more safer option then just setting such a way that it doesn't ask for password ( still you need to save your password somewhere to make firestarter start automatically !!! , because thist s/w itself needed to have root privillage ) ...
njoy ....
Friday, September 5, 2008
free PDF converter ....
Perhaps , the acrobat reader is one of the most downloaded junk on internet ... But it doesn't allow you to create PDF documents ....
you may ask ... Why need PDF document ? ... well , one of the reason is , with its help you can create document a bit difficult to edit for others ... also they can't simply just copy and paste your document for their use .. ( if you have disabled that function ) ...
But to make a pdf document , you are needed to buy adobe acrobat , sure that i don't want to do ... this software .. "doPDF free converter" is fine for me .... doPDF is a PDF converter for both personal and commercial use. Using doPDF you can create searchable PDF files by selecting the Print command from virtually any application. With one click you can convert your Microsoft Excel, Word, or PowerPoint documents or your emails and favorite Web sites to PDF files. doPDF installs itself as a virtual printer driver so after a successful installation will appear in your Printers and Faxes list.
njoy ...
Thursday, September 4, 2008
MEWU - Scene 3 ... Playing with DOCK

Well , people who use MACs , must be loving its famous "dock" thing ... and i am sure that windows lovers must be feeling jealous for that dock in Macs , though they can enjoy same dock feature for windows too but still its not native application ... they need 3rd party softwares like "rocket dock" or "object dock" right ??
It's true for linux / Ubuntu too ... here they use software ... "Cairo Dock" which is perhaps the most common and most famous dock around ubuntiens !!! ... but it is not available by default in synaptic manager , we have to add 3rd party software string ...
deb http://repository.cairo-dock.org/ubuntu gutsy cairo-dock
and then , click on reload in synaptic manager ....and then seach "cairo" in it .. it will show cairo dock now ... but don't forget to choose both "cairo-dock" and "cairo-dock plugins" .... and apply .. and dinggggg , you are done .... if you prefer a bit harder way , then take a look at this official ubuntu help ...
launch it via , applications -> system tools -> cairo dock ...
But here comes one problem ... it will not launched automatically again when system is rebooted !!! ... to do it ... go to system -> preferances -> sessions , in it "startup programs" and just click on "add" , and write what ever you like for name and comment , but in command type "cairo-dock" ( ofcourse without quotes.. ) ... and it will be launched automatically with every reboot !!!
enjoy ....
Archive
-
▼
2008
(81)
-
►
October
(12)
- Eyecandy cursor for Desktop !!
- Beware of What you Type ???
- Some routers are susceptible to SNMP injection !!!
- Converting Ordinary FlashDrive into Smart Drive !!
- What's Wrong with Aussie Companies ???
- MEWU - Scene 7 ... IDS for my Network ....
- Cloud Computing ..... future of Computing !!!
- Subsubstitute of MS Office !!!
- List the Folders ...
- Surf Anonymously !!!
- The DarkSide of LinuX !!!!
- What is "ClickJacking" ??
-
►
September
(18)
- Lyrics with Song ...
- Beware of PDFs ???
- Make the way for P4P .......
- MEWU - Scene 6 ... Want to replace FireFox ??
- (Un)Official Chrome for Linux !!!
- Find the Bots in your computer !!!
- MD5 ..... cross check the integrity ...
- Free AntiVirus for One Year !!!
- Top 10 Linux Distros !!!
- Useful Add-Ons for FireFox ...
- MEWU - Scene 5 ... Playing With Shark !?!?
- MEWU - Scene 4 ... GUI Firewall ..
- free PDF converter ....
- MEWU - Scene 3 ... Playing with DOCK
-
►
October
(12)
Tags
- antivirus (5)
- cloud computing (3)
- computer (7)
- eyecandy (2)
- firefox (5)
- free (13)
- information (23)
- internet (59)
- linux (6)
- MEWU (9)
- My First Birthday.... (1)
- news (52)
- security (21)
- software (37)
- technology (27)
- ubuntu (12)
- vulnerability (22)
- windows (42)
- windows xp (4)
Creative Commons
Random Thoughts .... by Gaurang is licensed under a Creative Commons Attribution-Noncommercial-Share Alike 3.0 United States License.
